소프트웨어 Toggle Defender.bat
2022.12.22 09:28
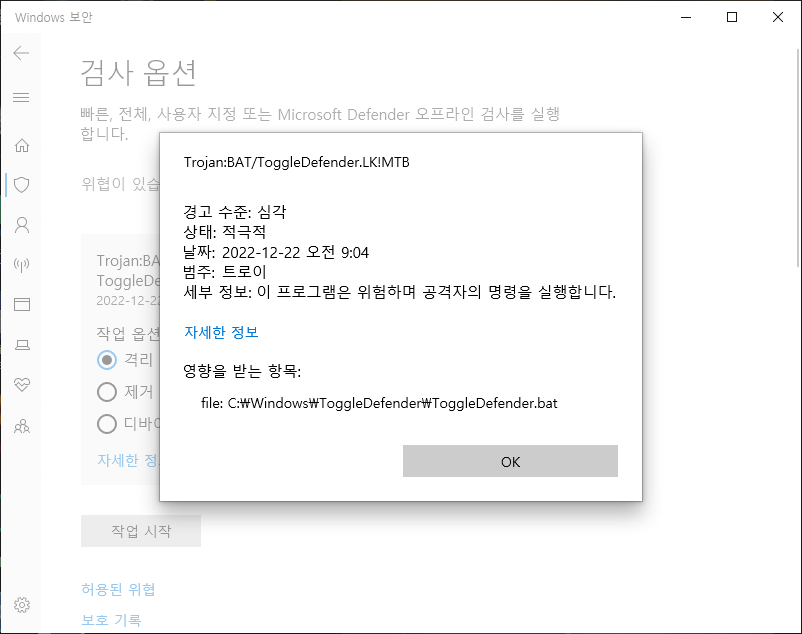
간만에 디펜더 검사를 했는데
Toggle Defender.bat 검출됩니다.
평소에는 디펜더 꺼놓고 사용합니다.
마우스 우클릭으로 디펜더 온오프 합니다.
혹시 이파일이 디펜더 온오프 하는 파일일까요?
아니면 지워야하는 파일일까요?
날씨가 많이 춥네요. 건강 잘챙기시고 연말연시 잘 보내시길 바랍니다~^^
ToggleDefender.bat
@(echo off% <#%) &title Toggle Defender, AveYo 2021-08-03
set "0=%~f0"&set 1=%*&powershell -nop -win 1 -c iex ([io.file]::ReadAllText($env:0)) &exit/b ||#>)[1]
## Changelog: also toggle store, chredge smartscreen + pua; prevent ui lockdown (2); unblock exe in chredge
sp 'HKCU:\Volatile Environment' 'ToggleDefender' @'
if ($(sc.exe qc windefend) -like '*TOGGLE*') {$TOGGLE=7;$KEEP=6;$A='Enable';$S='OFF'}else{$TOGGLE=6;$KEEP=7;$A='Disable';$S='ON'}
## Comment to hide dialog prompt with Yes, No, Cancel (6,7,2)
if ($env:1 -ne 6 -and $env:1 -ne 7) {
$choice=(new-object -ComObject Wscript.Shell).Popup($A + ' Windows Defender?', 0, 'Defender is: ' + $S, 51)
if ($choice -eq 2) {break} elseif ($choice -eq 6) {$env:1=$TOGGLE} else {$env:1=$KEEP}
}
## Without the dialog prompt above will toggle automatically
if ($env:1 -ne 6 -and $env:1 -ne 7) { $env:1=$TOGGLE }
## Comment to not relaunch systray icon
$L="$env:ProgramFiles\Windows Defender\MSASCuiL.exe"; if (!(test-path $L)) {$L='SecurityHealthSystray'} ; start $L -win 1
## Comment to not hide per-user toggle notifications
$notif='HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Windows.SystemToast.SecurityAndMaintenance'
ni $notif -ea 0|out-null; ri $notif.replace('Settings','Current') -Recurse -Force -ea 0
sp $notif Enabled 0 -Type Dword -Force -ea 0; if ($TOGGLE -eq 7) {rp $notif Enabled -Force -ea 0}
## Cascade elevation
$u=0;$w=whoami /groups;if($w-like'*1-5-32-544*'){$u=1};if($w-like'*1-16-12288*'){$u=2};if($w-like'*1-16-16384*'){$u=3}
## Reload from volatile registry as needed
$script='-nop -win 1 -c & {$AveYo='+"'`r`r"+' A LIMITED ACCOUNT PROTECTS YOU FROM UAC EXPLOITS '+"`r`r'"+';$env:1='+$env:1
$script+=';$k=@();$k+=gp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0;iex($k[0].ToggleDefender)}'
$cmd='powershell '+$script; $env:__COMPAT_LAYER='Installer'
## 0: limited-user: must runas / 1: admin-user non-elevated: must runas [built-in lame uac bpass removed]
if ($u -lt 2) {
start powershell -args $script -verb runas -win 1; break
}
## 2: admin-user elevated: get ti/system via runasti lean and mean snippet [$window hide:0x0E080600 show:0x0E080610]
if ($u -eq 2) {
$A=[AppDomain]::CurrentDomain."DefineDynamicAss`embly"(1,1)."DefineDynamicMod`ule"(1);$D=@();0..5|%{$D+=$A."DefineT`ype"('A'+$_,
1179913,[ValueType])} ;4,5|%{$D+=$D[$_]."MakeB`yRefType"()} ;$I=[Int32];$J="Int`Ptr";$P=$I.module.GetType("System.$J"); $F=@(0)
$F+=($P,$I,$P),($I,$I,$I,$I,$P,$D[1]),($I,$P,$P,$P,$I,$I,$I,$I,$I,$I,$I,$I,[Int16],[Int16],$P,$P,$P,$P),($D[3],$P),($P,$P,$I,$I)
$S=[String]; $9=$D[0]."DefinePInvokeMeth`od"('CreateProcess',"kernel`32",8214,1,$I,@($S,$S,$I,$I,$I,$I,$I,$S,$D[6],$D[7]),1,4)
1..5|%{$k=$_;$n=1;$F[$_]|%{$9=$D[$k]."DefineFie`ld"('f'+$n++,$_,6)}};$T=@();0..5|%{$T+=$D[$_]."CreateT`ype"();$Z=[uintptr]::size
nv ('T'+$_)([Activator]::CreateInstance($T[$_]))}; $H=$I.module.GetType("System.Runtime.Interop`Services.Mar`shal");
$WP=$H."GetMeth`od"("Write$J",[type[]]($J,$J)); $HG=$H."GetMeth`od"("AllocHG`lobal",[type[]]'int32'); $v=$HG.invoke($null,$Z)
'TrustedInstaller','lsass'|%{if(!$pn){net1 start $_ 2>&1 >$null;$pn=[Diagnostics.Process]::GetProcessesByName($_)[0];}}
$WP.invoke($null,@($v,$pn.Handle)); $SZ=$H."GetMeth`od"("SizeOf",[type[]]'type'); $T1.f1=131072; $T1.f2=$Z; $T1.f3=$v; $T2.f1=1
$T2.f2=1;$T2.f3=1;$T2.f4=1;$T2.f6=$T1;$T3.f1=$SZ.invoke($null,$T[4]);$T4.f1=$T3;$T4.f2=$HG.invoke($null,$SZ.invoke($null,$T[2]))
$H."GetMeth`od"("StructureTo`Ptr",[type[]]($D[2],$J,'boolean')).invoke($null,@(($T2-as $D[2]),$T4.f2,$false));$window=0x0E080600
$9=$T[0]."GetMeth`od"('CreateProcess').Invoke($null,@($null,$cmd,0,0,0,$window,0,$null,($T4-as $D[4]),($T5-as $D[5]))); break
}
## Cleanup
rp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0
## Create registry paths
$wdp='HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender'
' Security Center\Notifications','\UX Configuration','\MpEngine','\Spynet','\Real-Time Protection' |% {ni ($wdp+$_)-ea 0|out-null}
## Toggle Defender
if ($env:1 -eq 7) {
## enable notifications
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' Notification_Suppress -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' UILockdown -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' Notification_Suppress -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' UILockdown -Force -ea 0
## enable shell smartscreen and set to warn
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' EnableSmartScreen -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' ShellSmartScreenLevel 'Warn' -Force -ea 0
## enable store smartscreen and set to warn
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost -ea 0 |% {
sp $_.PSPath 'EnableWebContentEvaluation' 1 -Type Dword -Force -ea 0
sp $_.PSPath 'PreventOverride' 0 -Type Dword -Force -ea 0
}
## enable chredge smartscreen + pua
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 1 -Type Dword -Force -ea 0
}
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenPuaEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 1 -Type Dword -Force -ea 0
}
## enable legacy edge smartscreen
ri 'HKLM:\SOFTWARE\Policies\Microsoft\MicrosoftEdge\PhishingFilter' -Force -ea 0
## enable av
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection' DisableRealtimeMonitoring -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender' DisableAntiSpyware -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' DisableAntiSpyware -Force -ea 0
sc.exe config windefend depend= RpcSs
net1 start windefend
kill -Force -Name MpCmdRun -ea 0
start ($env:ProgramFiles+'\Windows Defender\MpCmdRun.exe') -Arg '-EnableService' -win 1
} else {
## disable notifications
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications 1 -Type Dword -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' Notification_Suppress 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' UILockdown 0 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications 1 -Type Dword -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' Notification_Suppress 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' UILockdown 0 -Type Dword -Force -ea 0
## disable shell smartscreen and set to warn
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' EnableSmartScreen 0 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' ShellSmartScreenLevel 'Warn' -Force -ea 0
## disable store smartscreen and set to warn
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost -ea 0 |% {
sp $_.PSPath 'EnableWebContentEvaluation' 0 -Type Dword -Force -ea 0
sp $_.PSPath 'PreventOverride' 0 -Type Dword -Force -ea 0
}
## disable chredge smartscreen + pua
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 0 -Type Dword -Force -ea 0
}
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenPuaEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 0 -Type Dword -Force -ea 0
}
## disable legacy edge smartscreen
sp 'HKLM:\SOFTWARE\Policies\Microsoft\MicrosoftEdge\PhishingFilter' EnabledV9 0 -Type Dword -Force -ea 0
## disable av
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection' DisableRealtimeMonitoring 1 -Type Dword -Force
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender' DisableAntiSpyware 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' DisableAntiSpyware 1 -Type Dword -Force -ea 0
net1 stop windefend
sc.exe config windefend depend= RpcSs-TOGGLE
kill -Name MpCmdRun -Force -ea 0
start ($env:ProgramFiles+'\Windows Defender\MpCmdRun.exe') -Arg '-DisableService' -win 1
del ($env:ProgramData+'\Microsoft\Windows Defender\Scans\mpenginedb.db') -Force -ea 0 ## Commented = keep scan history
del ($env:ProgramData+'\Microsoft\Windows Defender\Scans\History\Service') -Recurse -Force -ea 0
}
## PERSONAL CONFIGURATION TWEAK - COMMENT OR UNCOMMENT #rp ENTRIES TO TWEAK OR REVERT
#sp $wdp DisableRoutinelyTakingAction 1 -Type Dword -Force -ea 0 ## Auto Actions off
rp $wdp DisableRoutinelyTakingAction -Force -ea 0 ## Auto Actions ON [default]
sp ($wdp+'\MpEngine') MpCloudBlockLevel 2 -Type Dword -Force -ea 0 ## Cloud blocking level HIGH
#rp ($wdp+'\MpEngine') MpCloudBlockLevel -Force -ea 0 ## Cloud blocking level low [default]
sp ($wdp+'\Spynet') SpyNetReporting 2 -Type Dword -Force -ea 0 ## Cloud protection ADVANCED
#rp ($wdp+'\Spynet') SpyNetReporting -Force -ea 0 ## Cloud protection basic [default]
sp ($wdp+'\Spynet') SubmitSamplesConsent 0 -Type Dword -Force -ea 0 ## Sample Submission ALWAYS-PROMPT
#rp ($wdp+'\Spynet') SubmitSamplesConsent -Force -ea 0 ## Sample Submission automatic [default]
#sp ($wdp+'\Real-Time Protection') RealtimeScanDirection 1 -Type Dword -Force -ea 0 ## Scan incoming file only
rp ($wdp+'\Real-Time Protection') RealtimeScanDirection -Force -ea 0 ## Scan INCOMING + OUTGOING file [default]
#sp $wdp PUAProtection 1 -Type Dword -Force -ea 0 ## Potential Unwanted Apps on [policy]
rp $wdp PUAProtection -Force -ea 0 ## Potential Unwanted Apps off [default]
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' PUAProtection 1 -Type Dword -Force -ea 0 ## Potential Unwanted Apps ON [user]
#rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' PUAProtection -Force -ea 0 ## Potential Unwanted Apps off [default]
## even with "smartscreen" off you still need to unblock exe to download Firefox (sic) & other programs [F][F][S] microsoft!
$LameEdgeExtBlockWithSmartScreenOff='HKLM:\SOFTWARE\Policies\Microsoft\Edge\ExemptDomainFileTypePairsFromFileTypeDownloadWarnings'
ni $LameEdgeExtBlockWithSmartScreenOff -Force -ea 0|out-null ## add other extensions following the example below (increment 1)
sp $LameEdgeExtBlockWithSmartScreenOff '1' '{"file_extension": "exe", "domains": ["*"]}' -Force -ea 0
# done!
'@ -Force -ea 0; $k=@();$k+=gp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0;iex($k[0].ToggleDefender)
#-_-# hybrid script, can be pasted directly into powershell console
댓글 [4]
-
타천사둘리 2022.12.22 09:54
-
즐거운컴 2022.12.22 12:23
감사합니다~ 메리 크리스마스~
-
zerojiddu 2022.12.22 10:38 디펜더 완전정지는 이렇게 복잡하게 할 필요 없어요.
설정까지 다 건드리면 나중에 또
복잡한 정상복원 스크립트를 길게 만들어야 됩니다.
디펜더 레지값 변경할 TrustedInstaller 권한만 가지면(방법은 제 작성글에도 있고,
다른 분들도 제시한게 있어요. 이 방법들 모두,
목표는 관리자보다 높은 윈도우 권한을 가지는 겁니다.)
디펜더가 정상실행때
11개 서비스 시작유형 레지값만 한꺼번에 바꿔버리면
디펜더 실시간 감시에도 전혀 안걸리고, 기존 설정도 그대로 두고요.
파워쉘에서 이것만 치면
다음 부팅때 디펜더가 완전 전멸합니다. 디펜더 방화벽 포함.
밑의 숫자는 기본값이고 저 숫자를 모두 4로만 바꾸면 됩니다.
# (0=boot, 1=system, 2=automatic, 3=manual, 4=disabled)
$regpath='HKLM:\SYSTEM\CurrentControlSet\Services'
Set-ItemProperty -Path ($regpath+"\WinDefend") -Name Start -Value 2
Set-ItemProperty -Path ($regpath+"\WdFilter") -Name Start -Value 0
Set-ItemProperty -Path ($regpath+"\WdNisDrv") -Name Start -Value 3
Set-ItemProperty -Path ($regpath+"\WdNisSvc") -Name Start -Value 3
Set-ItemProperty -Path ($regpath+"\Wdboot") -Name Start -Value 0
Set-ItemProperty -Path ($regpath+"\SecurityHealthService") -Name Start -Value 3
Set-ItemProperty -Path ($regpath+"\mpssvc") -Name Start -Value 2
Set-ItemProperty -Path ($regpath+"\webthreatdefusersvc") -Name Start -Value 2
#Set-ItemProperty -Path ($regpath+"\webthreatdefusersvc_5a6b7") -Name Start -Value 2
Set-ItemProperty -Path ($regpath+"\webthreatdefusersvc_*") -Name Start -Value 2
Set-ItemProperty -Path ($regpath+"\webthreatdefsvc") -Name Start -Value 3
Set-ItemProperty -Path ($regpath+"\wscsvc") -Name Start -Value 2 -
즐거운컴 2022.12.22 12:24
감사합니다~ 메리 크리스마스~
| 번호 | 제목 | 글쓴이 | 조회 | 등록일 |
|---|---|---|---|---|
| [공지] | 질문과 답변 게시판 이용간 유의사항 | gooddew | - | - |
| 95655 | 윈 도 우| 파일공유 [1] | 천상천하 | 609 | 12-26 |
| 95654 | 윈 도 우| MBR 방식 윈도 시스템을 GTP 방식으로 문제 없이 전환하는 ... [6] | 써니7 | 987 | 12-26 |
| 95653 | 윈 도 우| 음 제가요. [2] | 심돌이 | 566 | 12-26 |
| 95652 | 기 타| pe에 대해 질문합니다. [6] | Question | 665 | 12-25 |
| 95651 | 윈 도 우| 저사양에서 윈도우11 설치방법이 없을까요? [6] | 빨간미소 | 1315 | 12-25 |
| 95650 | 하드웨어| 메인보드 바이오 업데이트 방법좀 알려 주세요 [3] | 놋지미 | 633 | 12-25 |
| 95649 | 하드웨어| usb쓰기금지(읽기전용) 해제 문의 [9] | 수사반장 | 2565 | 12-25 |
| 95648 | 모 바 일| sim카드를 넣지 않으면 wifi나 블루투스를 사용할 수 없나요? [2] | brucex | 765 | 12-24 |
| 95647 | 기 타| 요즘 휴대폰 교체시.. [16] | 한스 | 1277 | 12-24 |
| 95646 | 소프트웨어| ventoy-1.0.85 사용중인데 없었던 화면이 나타 납니다 [4] | 놋지미 | 825 | 12-24 |
| 95645 | 윈 도 우| 언제부터인가 이런 증상이 생겨서 사용할때마다 F1을 눌러... [5] | 한번에한걸음씩 | 1014 | 12-24 |
| 95644 | 기 타| 입문자님의 (우인님 Quantum PE 헤쳐모여 설치 체험기) 따... [7] | Jirisan | 648 | 12-24 |
| 95643 | 윈 도 우| 부팅진입후 이런 문구가 계속 나옵니다. 제거 방법좀 요청... [10] | 배움의진지 | 1373 | 12-23 |
| 95642 | 모 바 일| 안드로이드 태블릿 여러대 셋팅 방법 있나요? [2] | 흠냐리 | 501 | 12-23 |
| 95641 | 하드웨어| 사진을 복구 했는데도 볼 수가 없어요 도와주세요 [11] | 혹등고래 | 932 | 12-23 |
| 95640 | 윈 도 우| 요즘 윈도우 설치하는 방법이 이게 맞을까요? [17] | ljw8611 | 1122 | 12-23 |
| 95639 | 소프트웨어| 음악 플레이어 잘 아시는 분.. [6] | 열린하늘 | 977 | 12-23 |
| 95638 | 윈 도 우| 엣지 캐쉬나 쿠키 삭제하는 배치파일 [2] | 토르망치 | 824 | 12-23 |
| 95637 | 기 타| 우인님 뚱뚱한pe 벤토리로 부팅하니.. [11] | 빨간미소 | 1250 | 12-22 |
| 95636 | 하드웨어| 컴터 견적 부탁드립니다. [5] | 스카이피아 | 578 | 12-22 |

디펜더 OnOff 파일이 맞는 듯 합니다.